Set up strong defences against cyber crime.
Get in touch to find out more
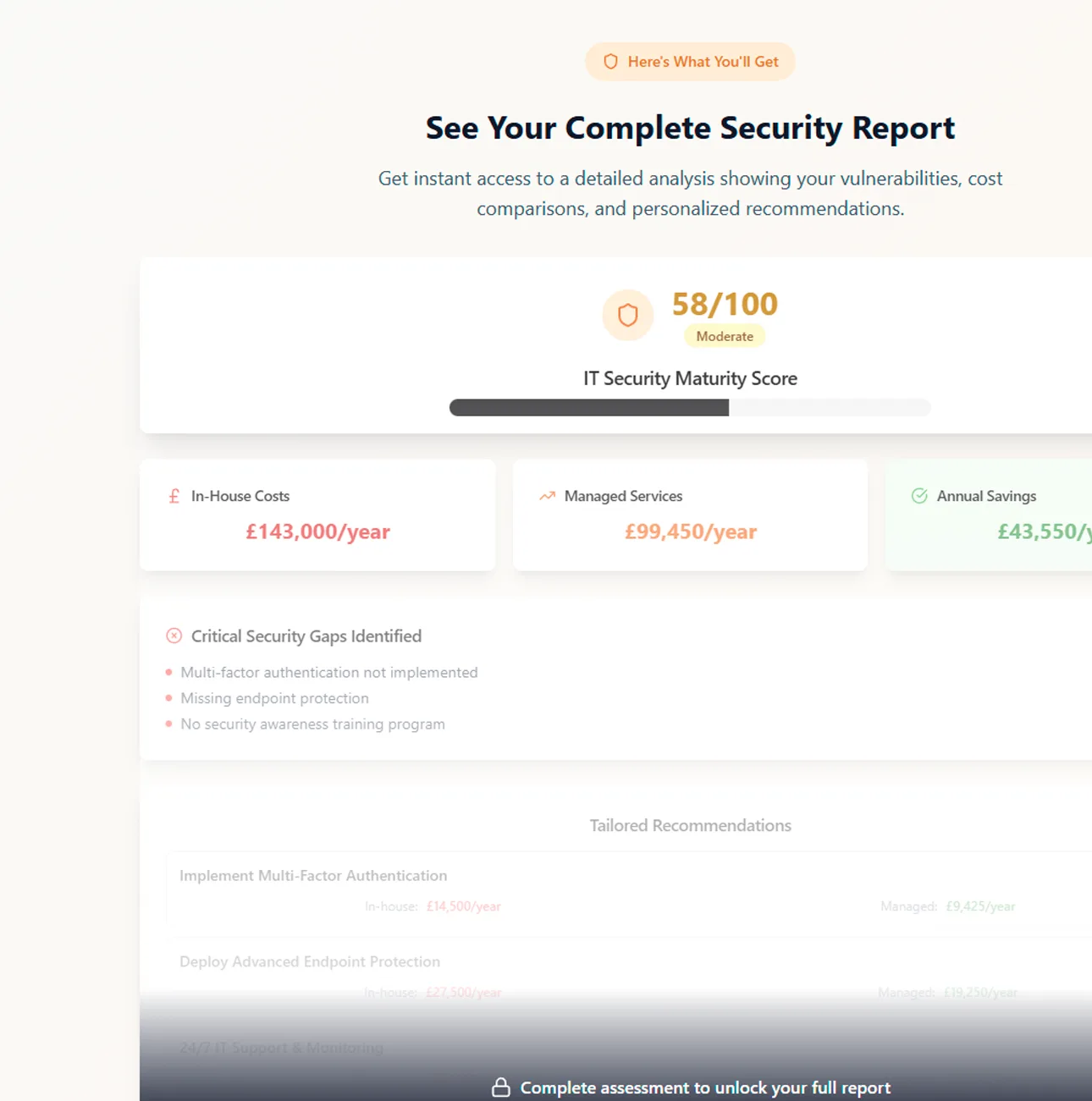
The pace that cyber crime moves at makes it very difficult for a business owner to keep abreast of the changes, let alone understand the ins and outs of protecting your network and people against cyberthreats. Gone are the days of being able to do an internet search and implement a solution that will protect your business.
Nowadays, an effective Cyber Security strategy involves several layers of protection providing the necessary cyber resilience for your IT infrastructure, systems and people. We'll look after your data security, cloud security and provide threat intelligence to help you avoid potential risks.

Threats from malicious software are managed automatically. Our systems engineers are also alerted and actively customise threat protection based on the information they receive.





Proactive detection & maintenance – security threats constantly evolve, by using a behavioural-based system that compares files to a known database can allow us to prevent attacks.
Detection – software, hardware, email and cloud-based services are all connected to a network or the internet in some shape or form. Using multiple layers of software and hardware to identify malicious or unusual behaviour across all platforms allows protection or instant remediation minimising the risk to your business.
Remediation – good remediation is about isolation of the threat in the first place to ensure the business can continue to function. Following this, any vulnerabilities can be worked on without the pressure of down-time.
Software as a Service (SaaS) Backup – Recovery from malicious encryption of data, accidental or malicious deletion is not included as a service from Microsoft and most other cloud providers. We therefore provide access to a reputable back up service and actively encourage our clients to back up their data and put a business continuity/disaster recovery plan in place ahead of any catastrophic event preventing them from accessing their data.
Identity Protection - Do you keep all your passwords on a notepad or in spreadsheet? When you reset passwords, do you use a few that you can remember? Do you ever waste time having to reset passwords because you can't remember it? You can enable multi-factor authentication (MFA), Single Sign-on (SSO), and use a Password Manager. A good password manager can even alert when your current passwords are going up for sale on the dark web!
Reporting – building a cyber profile of your business is hugely beneficial for identifying potential weaknesses in your cyber security strategy. The patterns identified through consistent reporting inform a tailored approach allowing you to invest only in necessary solutions