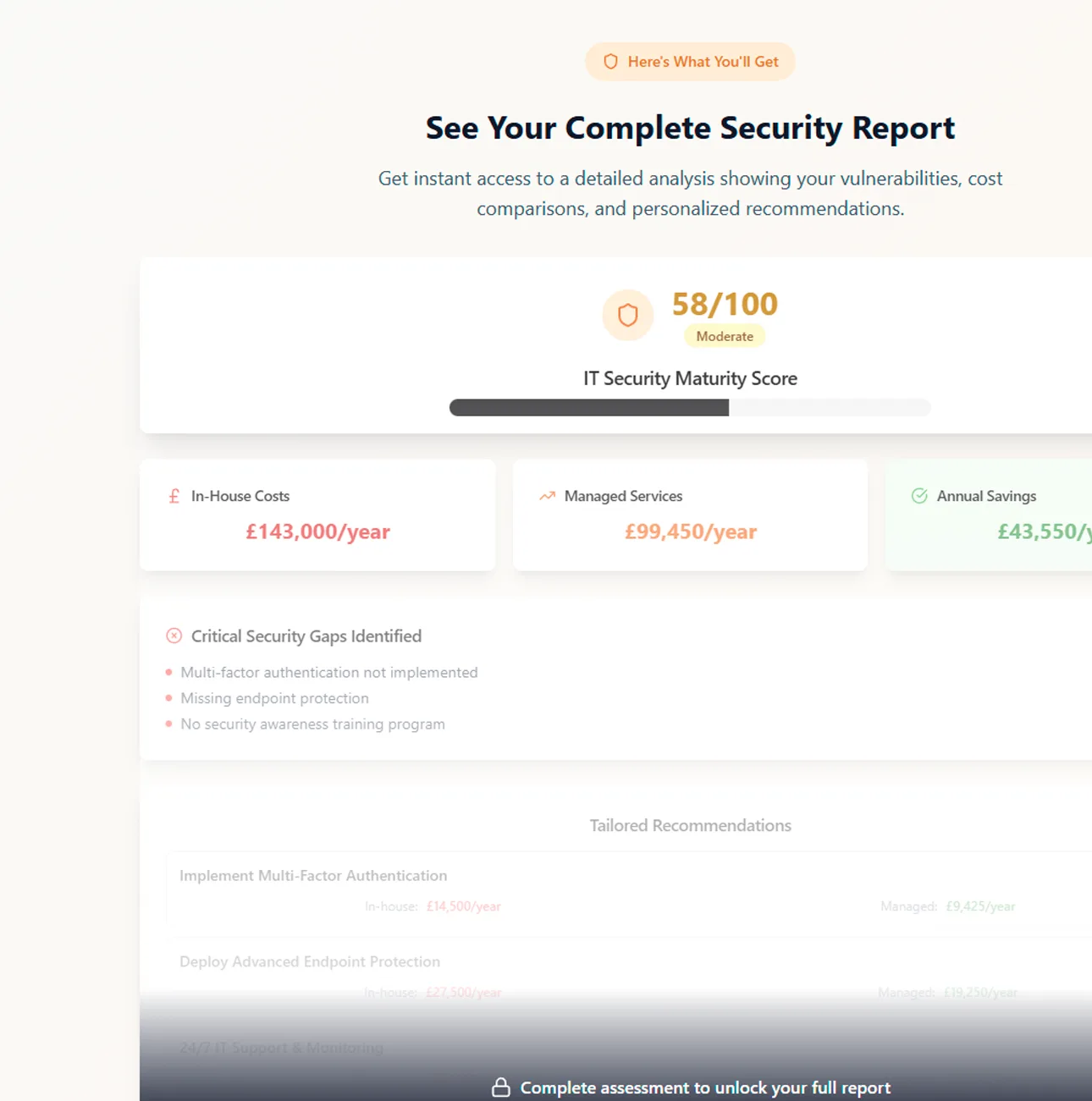
These days having a password is not enough. If you want to protect your data from hackers then you need another layer of protection – this layer is multi-factor authentication or MFA.
Essentially, multi-factor authentication (MFA) surrounds your login credentials with an additional layer of protection. You can compare having a weak password, like the standard “welcome1” to being in a busy town, and leaving your car unlocked in the high street with the keys just lying in the glove box. If you have a strong password, that’s the equivalent of leaving your car in the busy high street parked up. You’ve got the keys but you’ve left it unlocked. Then, the next level is MFA which is the equivalent of locking your car and keeping the keys in your pocket. MFA gives you that extra level of security and peace of mind, knowing that it’s going to be very difficult for someone to break in. In a nutshell, to adequately protect your systems, you absolutely need to implement MFA.
To put it bluntly, if you told somebody that they needed to lock their car, they’d agree with you. It’s obvious that you have to lock your car, if you don’t want to get it (or the contents of it) stolen. It’s the same with MFA. It needs to be standard practice.
The benefits of multi-factor authentication (MFA) are best combined with a strong password. If you have MFA enabled, you don’t really need to worry as much about rotating your passwords. There’s a common view that you should change your password every 90 days, or thereabouts. However, what if you didn’t change your password every so often, but you did have MFA?
Well, for example, you might accidentally fill in a web enquiry form that was fake and put your username and password for your Microsoft account in there allowing the hackers to get hold of this information. When they go to actually log on to your system, through your Microsoft 365 portal, they will be challenged before they get all the way in. They will be prompted for a six digit code that has been sent, asking them to provide the code at that point. However, it’s you who will receive a notification on your mobile phone or a text message not them. You’ll then be wondering why you are getting one of these codes. And at that point, you can just cancel it.
The thing is, if you’re only expected to produce a six digit verification code from an authenticator app, then you’ll never know if anyone has actually tried to access your account. The important point here is that quite often it is just a six digit code that’s generated from an authenticator app that is asked for. When that occurs, you won’t know if somebody is trying to access your account with the credentials that they’ve lifted, unless a managed services and security provider is monitoring your sign ins.
For example, you’ll probably experience it with the bigger email providers, where they will email you saying they have noticed some suspicious activity on your account and, more often than not, it’s just yourself that’s logged into it, perhaps from a different device or location. There are however a huge number of accounts where people don’t ever find out about their suspicious activity. They’ll never know that they’ve had something like 150 login attempts on their username and password for either their Gmail or Microsoft 365 accounts.
And that’s why it’s so important to have some kind of security policy and some kind of security monitoring set up with a managed services and security provider or internal IT department. Another option some businesses implement is automated alerting. Those are a few ways to ensure that you are aware of any security issues when they happen. This alerts you so that you can then change your password securing your account.
Every system that you log on to via the internet should offer multi-factor authentication (MFA), and we’d recommend that you always make that part of your remit when looking for a system. So, an example would be when we were looking for an HR management system; one of the systems was very good, but didn’t have any security features and didn’t include MFA. And for that reason alone, we decided not to go ahead with that system and ultimately chose a system that had MFA built in.
You may encounter systems that will not offer multi-factor authentication (MFA) but might offer what’s known as single sign on or SSO. Single sign on allows you to integrate one of your services, like Microsoft 365, as the system that you can use to log on with, so where you don’t have the ability to have MFA, SSO is a way around that where you can use your Microsoft ID to sign on to other services.
One of the concerns that we have with multi-factor authentication (MFA) is that people don’t always want to use their personal mobile phone to receive a code, even though, if it is a text message, it is free, so from that point of view, there’s not a problem.
However, you can buy a USB key that you can plug in to your laptop that will offer you MFA capability. The product that we’ve looked at is YUBIkey. This is simply a USB security key that you can register with Microsoft, Amazon, and all the many different providers and it means that you can’t access these sites unless you’ve got this USB security key plugged into your laptop. It’s super safe, super small and a great way to offer MFA for your staff that maybe don’t want to use their personal mobile phone.
You still can get what’s known as an RFID (radio frequency for identification) token that constantly rotates a six digit code, although they are less common these days. You might see these gadgets from the bank where you get what looks like a little calculator. While they can work with most systems there’s definitely an overhead cost to getting them set up.
Another option is to receive multi-factor authentication prompts via a gadget or you can set up some systems, like the Microsoft system, so that it will actually call your nominated phone number. A voice will say: this is the Microsoft verification system. And then it’ll say: is this you trying to sign on. You can reply by voice to say that, yes, this is me, and authenticate it that way.
In summary, you can use many different forms of multifactor authentication (MFA). The main ones are:
The one thing that won’t cost you a thing is switching MFA on. For most systems it’s merely a feature that you can turn on. There may be a small cost of time to set up the applications, and to set up the people to the system. But that’s the only cost involved with making your data more secure. And as we said at the start, this is as normal as locking your car.
MFA is now an absolute given. You have to do it to protect your business and we’d also recommend doing it to protect your personal internet-based services as well. The main thing to remember is: it’s not if you ever get phished or hacked it’s when. And when you do, you want to have the best strategy in place and in that case, MFA is a no brainer.