In simple terms, cyber security encompasses any action taken to protect your company data, personal and sensitive information which you store online, on a server or in the cloud.
Cyber criminals are highly motivated to infiltrate any system where they can sequester valuable data and convert it into cash.
It’s big business – in a November 2020 Cyber Crime Magazine special report they estimated that if it were measured as a country, cybercrime would be the world’s third-largest economy after the U.S. and China.
As technology progresses, businesses are producing ever-greater amounts of data. This increases the opportunity for that data to be either compromised, destroyed, breached, exploited, stolen or held to ransom.
The following is a non-exhaustive list of some of the most prevalent cyber crime methods currently being deployed by cyber criminals:
This can be any method by which an unauthorised person gains access to sensitive data. It could be as simple as someone leaving a USB stick on a train, an inadvertent breach from human error or a system glitch. The vast majority of data breaches are malicious. In IBM’s recently published annual Threat Intelligence Index they reported a 160% increase in data theft activity since 2019.
This is where people or automated systems are trying to access any system through any means possible. The simplest version is a brute force attack where a hacker finds access to a log in screen of some description and then simply applies a programme to try as many user and password combinations as it can until it cracks in.
A famous example of hacking is Gary McKinnon, a Scottish systems administrator, who between 2001 and 2002 allegedly immobilised US military computer systems following the 9/11 attacks.
In a BBC interview in 2005 he said: “I found out that the US military use Windows and having realised this, I assumed it would probably be an easy hack if they hadn’t secured it properly.”
Using commercially available software, Mr McKinnon probed dozens of US military and government networks. He found many machines without adequate password or firewall protection. So he simply hacked into them, he said.

The sending of deceptive emails aimed at luring a person to divulge data the hacker can use in some way. Hackers will invest a lot of time learning the habits of a company’s workforce so as to set them up. One scam is intercepting emails with PDF invoices attached and editing them with their own bank account details.
Is literally malicious software. Designed to disrupt, damage or spy on systems to build up a picture of a person’s habits or online activity it comes in several forms including viruses, ransomware and spyware. A common method of delivery is via spam email with malicious links.
Are one-dimensional ways of attacking a system. The intention behind their use tends to be for disruptive or destructive purposes. They spread in slightly different ways. A virus is a type of malware that piggybacks on another computer programme and can replicate and spread. Worms don’t require an infected programme to be launched (like a virus does) they can spread across systems and networks by themselves. Trojans conceal malicious code within a potentially useful app. Only after a period of time is its true nature revealed when it does something harmful.
Is a form of malware designed to spy on a system and steal sensitive data or track online habits so that these can be exploited in some way including the creation of further malware designed in response to the data the spyware has provided.
This form of malware encrypts data and can only be unlocked with the correct password which is not given unless a ransom is paid to the hackers. According to IBM’s report It is the most common form of cyber attack (23% of attacks) ahead of data theft (13%) and server access (10%). The biggest ransomware attack on record occurred on the 3rd of July with the hacking of an IT firm in Florida that affected hundreds of businesses around the world. The hackers seized valuable customer data and demanded payment of $70 million for its return.

It used to be big corporates that were the preferred target for cyber criminals (they still are); however, like in any sector, small businesses spin off the back of larger businesses and this is also the case with hackers. Cyber crime has evolved.
Currently, the industry targets ANY business regardless of size, from automated attacks on small businesses with very little cyber security protection through to calculated and long-term campaigns against vast global enterprises. It can take over 100 days before a cyber threat is noticed within a business, by that time it is quite often too late.
A frequent reply from business owners when asked about their cyber security health is; “My business is small and pretty secure – it won’t happen to me”. Yet, according to Accenture’s Cost of Cybercrime Study, 43% of cyberattacks are aimed at small businesses.
Painful consequences of Cyber Crime include:
Each of these can significantly interrupt business functionality with far-reaching implications. Of considerable importance is the potential reputational damage of a data breach. Thanks to the internet, news disseminated about a company’s cyber incident will travel far and wide.
A Forbes article states that according to IDC “80% of consumers in developed nations will defect from a business because their personally identifiable information is impacted in a security breach”.
Reputation is an intangible asset that has significant value as it determines the relationships the company has, not only with current employees and clients, but prospects, future investors and employees.
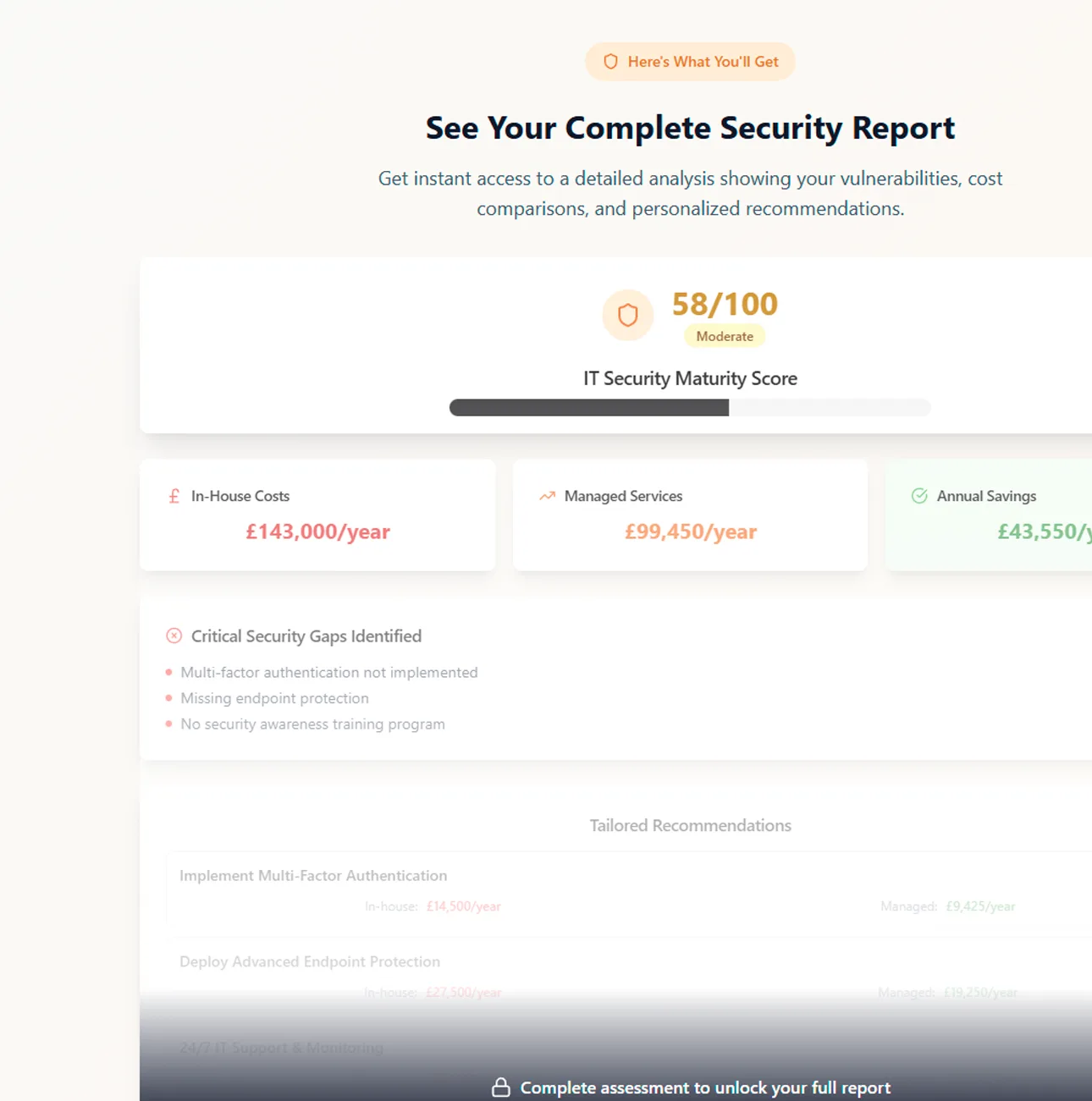
Clearly prevention is the best approach to avoid serious damage to your business. Working with a Managed Service & Security Provider (MSSP) to set up an effective cyber security strategy with layers of protection, alongside regular training, is your best defence